What It's Like Competing in Trace Lab's Search Part For The First Time
Over the weekend, I took part in a CTF with a goal of finding missing people, in many cases after the case has gone cold with the police. I don’t think I did very well, I’m certainly not qualified on how to tell you how to do well, but it was an amazing experience that put into perspective how basic cybersecurity skills often associated with maliciousness can be put to use for amazing good.
What is Search Party and who is Trace Labs?
According to Trace Labs, over 8 million people go missing worldwide every year; 500,000 people in the US alone in 2020. It’s an enormous problem that has not been solved by the digital advances of our time, and in fact, it may have gotten more complicated. There are more missing person databases to correlate, all at varying stages of currency and accuracy. There are more and more avenues to explore in social media. There are more jurisdictions. Correlating intelligence on missing persons is an evergrowing difficult task for law enforcement. Trace Labs says these difficulties ultimately mean that it is rare for missing persons and body recoveries to be successfully matched with known cases.

Trace Labs is a Not-For-Profit organization with a mission to solve this problem. Their goal is to crowdsource and modernize the collection of intelligence and leads on missing persons through open-source intelligence (OSINT). Trace Lab’s Search Party is like a CTF event, where competitors attempt to uncover flags or objective information. However, it is unique because no prepared environments, scenarios, or intentional traps and rabbit holes are built into the competition. No one from Trace Labs is out on the internet peppering out flags to be found. As a participant, you score points only by discovering real-world and actionable information on real missing person cases referred to Trace Labs by law enforcement organizations worldwide.
The format for Search Party is simple. You listen to a 1-hour briefing on Zoom, and then the platform opens up. Every team of up to 4 people gets the same 4-6 missing person cases to work on. You have 4 hours to submit flags, which must be accurately linked to, and documented with evidence that the flag is valuable to the case with supporting evidence that it is linked to the missing person or a person of interest related to the case. Speculation is frowned upon and not allowed, and judges will deny flag submissions if your supporting evidence is not thought out. Anything you gather for the case must be obtained in a publically accessible place and in a passive manner. Actively speaking to a family member of the missing person, or other active investigation methods, will get you banned and potentially reported for interfering with an active investigation. After 4 hours, all flags are tallied up by team, and awards are handed out.
Preparing for the Trace Lab’s Search Party
I will say that I did not prepare enough right off the bat. I found out about the 2022.3 CTF relatively late in February, which left not a lot of time to prepare. I was and am still busy with NCL preparations, college coursework, getting back on the horse for certifications alongside my full-time job. As someone in the IT space, I naively thought, “how hard could OSINT be?” After all, my day job is often chasing down leads on esoteric system bugs that first surfaced in 2013, have 1 closed and unresolved Stack Overflow post, and seem to have only affected me and one other person on the planet that closed their Technet forum post with “Nevermind, fixed it.” with zero follow up on what the root cause was. So, I’m not saying I phoned it in, but my preparation ended up being vanilla.
Step 0: Get a VPN
Everyone in the world is already well marketed on why you should use a VPN, blah blah your privacy, blah blah protect your financial information, blah blah Netflix. I picked a provider in the US and paid for their lowest plan. I selected a US VPN provider because the exercise for Search Party is not to hide from the law. It’s to appear on social media like you are coming from the part of the world you say you are coming from.
Creating Sock Puppet Accounts for Social Media
The main thing I didn’t have on hand was a pile of sock puppets to use on social media accounts. For those who don’t know, a sock puppet or persona is a fake identity used to cloak the identity of the person actually browsing on social media. Obviously, there are nefarious reasons you would use a sock puppet, but for Search Party, the reason is pretty straightforward: you must be as quiet and unidentifiable as possible in the vent of a mistake that makes your presence known to family members or potentially even suspects.
First, I used https://randomuser.me/ to generate basic information for the socks. I was going to make a separate sock for each social media site but ended up going with just one persona. After coming up with information, I documented it in my Bitwarden instance as an Identity and created a folder for passwords to keep it organized and pastable. I made my first mistake here, which was I decided where my sock puppet’s geographical location would be before the event. This made my investigation more difficult as certain social media sites steered me towards matches within the state I had chosen for my sock puppet, not the state of a missing person.
In the future, I’ll prepare all the information for the sock puppet before the event, but I won’t execute on making accounts till after.
Next, I used https://thispersondoesnotexist.com/ to generate a fake profile image for my sock puppet. This is important because you don’t want to use someone’s actual face. For one, there is an ethical component of identity theft. More importantly, anyone can reverse image search that profile picture and figure out the sock puppet account is, at minimum, a catfish. After finding a face that I felt matched my persona, I took the result into Photoshop and cleaned up some of an AI-generated faces' typical quirks. Thinks like asymmetric makeup and jewelry, blurry hair strands, non-sensical soft backgrounds, etc. I also offset the face within the image, so it wasn’t perfectly centered, and rotated the image slightly. This imperfection will make it harder for sock puppet detection on social media sites to determine if the picture is generated or real. The perfect placement of the eyes of a face in an image can be a significant giveaway it’s fake.
Finally, I spent some time with AI text generators to create a headline for a certain professional social network, and profile bios for the rest. The advantage of using AI writers is that you can develop a lot of creative content that is naturely void of your writing style quickly. For example, I would simply prompt the AI for “Twitter bio for a 25 year old from Florida who went to X College” and it gave back mostly junk to be honest. However, after a dozen runs it assembled enough for me that looked authentic and like I would’ve never written it myself.
Using Cell Phone Trials to Register Sock Puppet Accounts
After creating the needed material for a believable sock puppet, I picked up a Mint SIM card from Best Buy for $2 and popped it into an old phone. Here, I potentially made my second OPSEC mistake in downloading the Mint app from my home IP address. This probably doesn’t matter in this instance, but Mint will have logged this IP. Again, not trying to hide from the law or nation-state with access to Mint’s systems (I hope.).
I popped the VPN App onto the Phone and setup the Mint trial with provides a temporary phone number. After receiving the phone number it is now simply a matter of going to all the social media account you want your sock puppet to exist in and registering them through the VPN. Fortunately, I experienced almost no trouble setting up since I used a phone number to verify, except for Google. Ultimately I didn’t need Google, but I felt like tying a Google account to the social media accounts gives the sock puppet authenticity.
Setting Up A Virtual Machine For Trace Lab’s Search Party
Trace Labs actually provides a virtual machine for OSINT, which is based off of Kali with all the pentesting tools removed. I ended up not using this, because I typically like to have my VMs not on my host for paranoidal and largely unfounded fears that somehow an attacker will hack my browser session on the VM and break out of the VM’s containment on to the host. If you’re going to go through the effort of making sock puppets and using a VPN, why have any risk of host information leaking into the VM as well.
This is the part of the preparation where I should’ve automated a lot more if I had more time. I ended up just using an Azure VM with Windows 10. The best thing about Azure is that even though it’s expensive, you don’t pay for anything but storage if the VM is off. I created the VM about a week in advance, signed in with a username related to the sock, and downloaded a couple OSINT apps such as buster, theHarvester, and I also created a Powershell Job to check my external IP and throw a notification into my window what has occurred, and starts an Azure Logic App which denies HTTP and HTTPS traffic out from my VM. This makes sure that traffic doesn’t leak from my VM’s real IP address, and serves an effective kill switch when I don’t want to just pull the NIC (since that would disconnect me too).
Overall, my VM didn’t fail me, but I did not do a great job of preparing the tools I might have wanted during the competition. Since the comptetition is only 4 hours long, you really need to be ready to go with nearly zero configuration needed at the start. There’s not a whole lot of time to download and setup tools as you realize you need them after beginning. You’ll see that I almost ended up exclusively in search engines because of this.
Brushing up on OSINT Skills
Lastly, I brushed up on my OSINT knowledge during the week before. That mostly comprised of Youtube videos and podcasts, and I’ve linked my three favorite below:
Competing in Trace Lab’s Search Party
I got up late in the morning, well-rested, and listened through a couple more podcast episodes before the briefing. I messaged briefly with my teammate from WGU, who was also experiencing this for the first time. We didn’t know what to expect or even how to plan ahead for how to divide work. I felt a slight sense of anxiety, not just because I had no idea what to expect or how prepared I was but also because I was aware I was about to become a part of someone else’s terrifying story. They would never know it, nor would their family, but for four hours, I would be paired with people who had already lived the worst days of their lives and had not seen justice or salvation from their crisis. Many of them are potentially no longer alive. I felt a sense of a responsibility that I must give my absolute best, for them, competition or not. That made the idea of personally not doing well even more anxiety-inducing.
At 2pm, the briefing Zoom call started. Tom Hocker and Robert Sell welcomed us all and explained the rules and purpose of what we were doing today. They told us what Trace Labs is and what it stands for, and why volunteers are more needed than ever to gather OSINT for investigators. We were humorously and then sternly reminded that if we got a missing person’s password that under no circumstances should we ever think about or attempt to reset it.
At 3pm, the platform opened, and six missing people sat in front of me, with everything the police knew attached to the story of the day they disappeared. The gravity of the task suddenly became very apparent, and the feeling that I had no idea what to do and that I didn’t prepare enough washed over me. I now had just an hour and a few minutes per person to find out as much as possible about them. No time to mull over details or time to break and think things over.
Person 1
The first person was missing in Australia. It was at this moment, I realized I had messed up my preparation. I had no idea how to research anything outside of the US or Europe. What social media was common? What government resources exist? No clue.
After 20 or so minutes, I decided I had to move on. I was having problems finding news articles, social media handles, or any information on the person. They were a digital ghost.
Person 2
Person 2 continued the theme of difficulty for the day. They were also missing from Australia. There was some more information on them. They seemed to have a professional life, and I was able to submit my first flag in the form of their broker license. Unfortunately, their social media was a dead end. I had assumed before the CTF started that the flow would go as follows:
- Find their social media
- Find pivot points from their social media
- Unravel their identity and their digital story
I used Sherlock for the first time to uncover their social media, which went well, but their posts were light in quantity and context and weren’t very interactive. I had to start fighting the doubt that I didn’t know what I was doing because I was sure other teams were finding what I was missing. Luckily, my teammate found another social media account for them, which netted us a couple of flags and kept us ahead of last place.
Person 3
By Person 3, I was already an hour in, and I felt absolutely amateur. Out of 180 teams, we were sitting nearly in last place, and part of that was because I had found one flag. At my current rate, I would contribute nothing of value. The feeling of dead weight took hold, but I pressed on.
Person 3 was, once again, from Oceania, New Zealand, to be specific. Are you sensing the pattern? I could feel a theme of my American-centric social media and OSINT knowledge being brushed aside. Apparently, I need to be more worldly.
Ultimately, neither my teammate nor I could get anything on Person 3. We were both struggling and felt in over our heads and that we had vastly overestimated our ability. We also realized that the top teams were putting in a magnitude more submissions than us, and we started to wonder what we were doing wrong.
Person 4
Person 4 was actually a somewhat prolific case, which was challenging because my understanding of the story is that the police generally knew what might have happened to them. Still, the person’s body had not been located. I found many news articles and found that most information had been publically made available already through the police and media, meaning those pieces of intel were not valid flags.
I got lucky and found their Linkedin profile, but they hadn’t interacted there. I spent a while longer trying to find anything relevant, and I finally started to submit a couple of flags. Ultimately, nothing spectacular, and I had to move on.
Person 5
By Person 5, I was becoming burnt out. To be honest, I don’t remember many details other than that they were Australian, and I ran into many of the issues. Digitally a ghost or I was just missing the mark finding emails and then social media for the person.
Person 6
Person 6 was American. From my experience talking to the other competitors, Person 6 was the most interesting and active online. I was able to get social media on them pretty quickly. Others had pieced together odd interactions between family members. I started to dig into background checks on the person. I found the highest value intel yet: Someone was updating this person’s phone number and address semi-regularly and over two years after they disappeared. The property addresses didn’t tie back to family members.
That foothold into finding relevant information woke me up, and for the first time today, I felt like I was actually doing something properly!
I found criminal records of the person and their partner, which painted a grim tale of their interactions with each other. Finally, I found social media, and I found the trail of breadcrumbs I thought would be so easy to see going into this. Unfortunately, time ran out. I submitted what I could, and I was happy to see that my last-ditch efforts moved my team from the bottom into the midfield!
Lessons Learned from Search Party and What I’ll Do Differently Next Time
After the Search Party, I was extremely humbled and mentally exhausted, but proud of the 500 points I pulled out in the last 30 minutes. I sat back, and deleted the VM as it had served its purpose. My team results were not much at all by the standards of the top team, but I had started to pick up on what I should be doing. All teams put together found a lot:
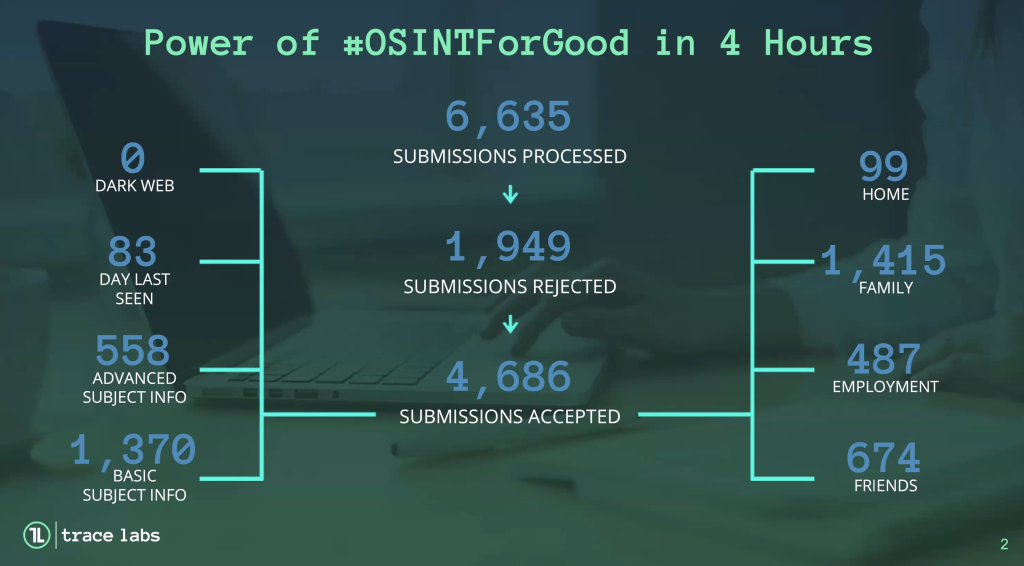
Overall, I was extremely happy I took part in this event and intend to do it again. Trace Labs was genuinely thankful of all the time the competitors volunteered, and they closed the debrief with a reminder that now the event is over, it’s time to let go. But, nowing what you find out about the missing people, that can be difficult, and you want to see them safely found. I was absolutely blown away by some of things the top teams found.

Looking back on Saturday, I took away the following things:
-
Maximimize the rubric. Trace Labs provides a rubric of types of information and their associated points. When you find a lead, it is important for the competition to submit that lead in as many contexts as it matches to maximize point values. I submitted many screenshots containing multiple types of information, but only got scored for 1 type.
-
Have a note template ready before the event starts for up to 6 cases. This will save time and let you just write out relevant information during the competition. I was on the backfoot trying to organize material into OneNote and the platform during the competition.
-
Being able to pivot quickly is critical to finding enough leads in a 4 hour window. I was rusty on many of the tools I used and I had to think a lot on how I wanted to pivot. Of the 4 hours, I probably spent 2 just trying to figure out what method to use to pivot onto more information. Tool usage should come as naturally as writing, unlike many CTFs with longer time frames, there isn’t much time to read documentation.
-
Be prepared to rebase yourself geographically, and consider creating your sock puppets in the general locale of your cases. Have the information ready, but don’t execute account creation until the case locations are known. You can make a social media account in under 5 minutes if you already have everything ready to be copy and pasted. Switch the VPN to the local location of the case and then make the sock puppet. I had to filter through so many irrelevant results because my profile was in the wrong geographical location. Having a sock puppet setup before hand is good if something goes wrong during the creation during the competition, but having a sock puppet purpose made in the correct locale will make life much easier.
-
The judge is there to determine if the flags you provide is relevant to the case, don’t self eliminate your own flags by guessing their relevancy. I realize in retrospect I did this a lot, and certinly costed my team points. As Trace Labs mentioned in the debrief, anything and everything related to an individual or associate can be useful. Even if the police already know all of the information found, our submissions serves as confirmation and independent verification that the police found what they could. So submit everything, as long as you’re not being disengenious about it.
-
OSINT is a broad skillset and topic. Like anything in technology, you are always a student of it if you choose to be, and there is always more to learn. Sometimes it is as simple as knowing what to type into Google, and knowing what public databases are available to search, but after today, those methods felt shallow and unhelpful and I was unable to learn enough in those short 4 hours to work my way through social media.
-
Don’t go in alone, get a team. An experienced team preferably. Knowledge transfer from Search Party veterans is worth its weight in gold.